News

A Trusted Wireless Environment
17 Mar 2020
The Evolution of Wi-Fi
With the rise of Internet-enabled devices, so did wireless security risks. In 2017, there were 8.4 billion connected devices and the volume is expected to hit 20.4 billion by 2020, according to analyst firm Gartner. When wireless devices are hacked, it can result in a wide range of issues, including denial of service, compromised personal data, and major infrastructure failures – all costing companies time and expense. Hackers prefer to go after the weak link in the security chain and it doesn’t take much to hack into a Wi-Fi network using easily accessible tools and a plethora of online how-to videos.
The Six Known Wi-Fi Threat Categories
- Rogue access points are connected to the authorized network, usually with an open SSID, allowing attackers to bypass perimeter security. They can be a physical access point (AP), or one created in software on a computer and bridged to the authorized network.
- Rogue clients are defined as clients that previously connected to a rogue access point or other malicious access point within the range of a private network. This client could have been victimized by a plethora of man-in-the-middle (MitM) attacks that include loading ransomworms, malware, or backdoors onto the client.
- Neighbor access point is an independent AP that is not under the control of network administrators. It provides access through a separate network and could be used to bypass internal security or content-filtering policies.
- Ad-hoc connection is a peer-to-peer Wi-Fi connection between clients that can circumvent perimeter security and allow clients to evade firewalls, and content and security controls.
- Evil twin access point is one that mimics a legitimate AP by spoofing its SSID and unique MAC address. Besides a commonly known physical access point, attackers can use software that utilizes Wi-Fi network adapters in standard laptops and tablets or certain native mobile devices to minimize their physical footprint and avoid drawing attention to large antennas, devices, or cables.
- Misconfigured access points are connected to your private network with a configuration that does not conform to your security policies and allows insecure connections. For example, if your Wi-Fi security policy is configured in Wi-Fi Cloud to only allow SSIDs to broadcast on your authorized APs with WPA2 encryption and an admin accidentally misconfigures an authorized AP to broadcast an open, unencrypted SSID, that AP would be considered misconfigured.
Pillars of a Trusted Wireless Environment
The Wi-Fi systems that you have been installing are no longer adequate. Your employees, vendors and guests rely on you to keep them safe and it is your responsibility to be knowledgeable about Wi-Fi security risks and how they impact your organization. As you face the responsibility of evolving your Wi-Fi networks to include security, you’re finding that many vendors, like Cisco Meraki, Aruba and Ruckus do not enable you with the right products.
Your organization needs technology and solutions that enable you to build a complete Trusted Wireless Environment. It is a framework for building a complete Wi-Fi network that is fast, easy to manage, and most importantly, secure. Businesses face the responsibility to build Trusted Wireless Environments protecting their employees and customers from hackers who easily exploit the weak or non-existent security of traditional Wi-Fi networks.
Companies that offer a Trusted Wireless Environment deliver on these three core pillars:
- Market-Leading Performance: You should never be forced to compromise security to achieve adequate performance to support your environment with the speed, connections and client density that it needs.
- Scalable Management: With easy set-up and management, you should be able control your entire wireless network, big or small, from a single interface and execute key processes to safeguard the environment and its users.
- Verified Comprehensive Security: Many vendors rely on ambiguity when it comes to delivering secure Wi-Fi. You need proof that your security solution defends your business against Wi-Fi attacks and can deliver on the following benefits:
- Provide automatic protection from the six known Wi-Fi threat categories
- Allow legitimate external access points to operate in the same airspace
- Restrict users from connecting to unsanctioned Wi-Fi access points
Miercom Test and Key Findings
Miercom – a widely recognized company that generates industry reports based on hands-on competitive testing – recently covered a ground-breaking, never-been-done series of tests, to determine how effectively an access point can support real-time applications such as voice, video, and data while simultaneously detecting and preventing the most common Wi-Fi security threats.
For each Wi-Fi threat, they recorded the time to detect and time to prevent using Wi-Fi equipment from WatchGuard, Aruba, Cisco Meraki, and Ruckus.
Test Details
Access points, firmware and management platforms used in all tests:
| Vendor | Access Point Model | Management Platform | Firmware |
|---|---|---|---|
| WatchGuard | AP420 | Wi-Fi Cloud | 8.5.0-658 |
| Aruba | AP335 | Aruba Central / Aruba Instant | 8.3.0.0_64659 |
| Cisco Meraki | MR53 | Meraki Cloud Controller | MR 25.11 |
| Ruckus | R710 | Zone Director 1200 | 10.1.1.0 |
In every Wi-Fi threat test case, IP multi-cast traffic was generated to keep the access points busy. In a real environment, APs need to be able to serve clients as well as provide security protection without impacting the quality of user experience. Multi-cast to unicast conversion was utilized in all APs and served to a total of 18 clients, with 6 on 2.4 GHz and 12 on 5 GHz. Spectrum analysis was performed continuously to confirm that no other APs nearby were utilizing channel 1 or 149-153 during the testing. Channel utilization did not exceed 60% for 2.4 GHz or 40% for 5 GHz during the tests.
Client devices used for continuous traffic generation during all Wi-Fi threat tests:
- 18 - Acer Laptops with Qualcomm Atheros 1x1 Wave 2 WLAN capability and Windows 10 OS
Rogue AP Test Details
Rogue APs are a dangerous Wi-Fi security threat where an AP is plugged into a private network by a nefarious person often broadcasting hidden SSID(s) so that attackers within range can gain access to internal network resources over the air. Common targets include credit card data (CDE or cardholder data environment), which is a serious PCI compliance risk, and building-automation controls for alarms, door locks, and video cameras.
.jpg)
Rogue Client Test Details
Any client previously connected to a rogue AP or other malicious AP within range of a private WLAN network is considered a rogue client. This client could have been victimized by a plethora of man-in-the-middle (MitM) attacks that include loading ransomworms, malware, or backdoors onto the client.

Neighbor AP (Misbehaving Client) Test Details
Environments such as offices, airports, healthcare locations, retail, and restaurants often contain a mixture of company-managed Wi-Fi client devices that are only intended to connect to company-managed SSIDs so that network security controls, encryption, and traffic visibility can be maintained, while public guest clients are not company-managed. In these environments, company-managed Wi-Fi clients should never be allowed to connect to nearby 3rd party, or neighbor, SSIDs. Doing so bypasses all important network security controls and traffic visibility for network administrators. For example, a point of sale (POS) handheld card reader that operates over Wi-Fi should only be allowed to connect to the private company-managed SSID within the restaurant and not nearby public hotspots or mobile/LTE Wi-Fi hotspots that are likely not encrypted and could expose sensitive information to attackers looking to intercept the data over the air. Another common example is in corporate offices where clever employees figure out, they can connect their company-managed smartphones, laptops and tablets to nearby public Wi-Fi hotspots or internal guest Wi-Fi SSIDs to bypass web content-filtering controls.

Ad-Hoc Network Test Details
It can be a security risk in certain environments when Wi-Fi clients connect directly to each other, as the traffic generated in this peer-to-peer session is invisible to network administrators.

Evil Twin AP Test Details
Evil twin APs are very dangerous, as victims typically have no idea that everything, they are sending over Wi-Fi is being intercepted by an attacker and typically the traffic is invisible to any network security controls. This makes the attack a very safe one for an attacker as usually there are no tracks left behind of the attack that could pinpoint the culprit. An evil twin is an AP where the attacker has copied and broadcasted the same SSID name as a legitimate AP within range and often spoofs the legitimate AP’s MAC address, thus creating an “evil” copy of the real AP. Victims’ Wi-Fi clients will auto-connect to evil twin APs as there is no apparent difference between the real AP and the evil AP. Once connected to an evil twin AP, the traffic a victim generates travels through a “man-in-the-middle,” allowing the attacker to intercept sensitive information and inject packets into the data stream to alter communications.

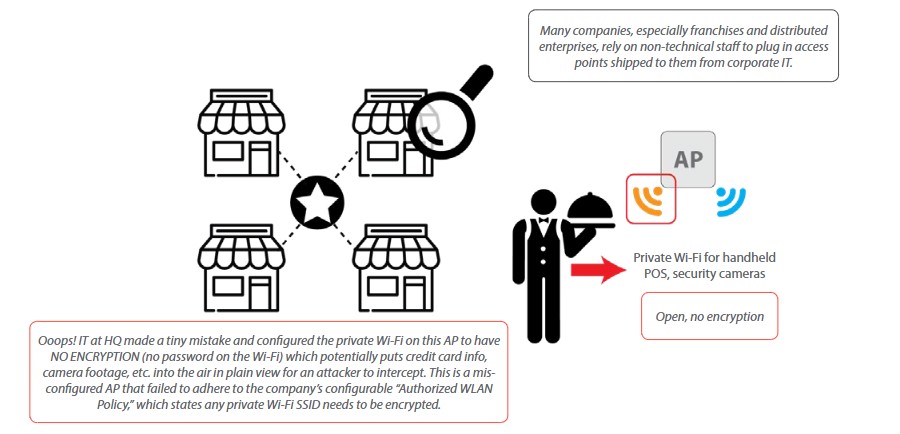
Misconfigured AP Test Details
In busy networks where new APs are being deployed, it can be too easy for network administrators to accidentally make a configuration mistake such as making a private SSID open with no encryption, potentially exposing sensitive information to interception over the air.
A misconfigured AP is one that has a configuration, such as one with encryption requirements, that do not adhere to network security policy.
Concurrent Threats Test Details
Crowded places like conference centers, train stations, airports, and concerts are perfect places for a hacker to take advantage of any and all Wi-Fi attack vectors. These busy environments are prime hunting grounds for attackers as they know people are usually under time pressure and distracted by their surroundings.
.jpg)
Test Results
| WatchGuard AP420 | Aruba IAP335 | Cisco Meraki MR53 | Ruckus R710 | |||||
| Test | Detect | Prevent | Detect | Prevent | Detect | Prevent | Detect | Prevent |
| Rogue AP | P | P | F | N/A | F | MP | F | N/A |
| Rogue Client | P | P | F | N/A | F | MP | N/A | MP |
| Neighbor AP | P | P | P | P | F | N/A | F | N/A |
| Ad-Hoc Network | P | P | F | N/A | F | N/A | P | N/A |
| “Evil Twin” AP | P | P | P | F | P | MP | P | F |
| Misconfigured AP | P | P | P | N/A | N/A | N/A | N/A | N/A |
| Concurrent Threats | P | P | F | F | F | F | F | F |
P = Pass
F = Fail
MP = Marginal Pass
N/A = Feature Not Supported
Key Findings for WatchGuard
- The ONLY vendor to automatically detect and prevent the six known Wi-Fi threat categories simultaneously while maintaining performance
- The ONLY vendor to support automatic detection and prevention of rogue APs and rogue clients
- The ONLY vendor to automatically detect and prevent endpoints from communications over ad-hoc Wi-Fi connection
- The ONLY vendor to automatically prevent connections to evil twin APs and dangerous connections to misconfigured APs such as private SSIDs without encryption
Download Miercom report at: www.watchguard.com/wifi-security-report
If you have additional questions regarding WatchGuard solutions, please, write us at watchguard@bakotech.com.

 Հայաստանի Հանրապետություն
Հայաստանի Հանրապետություն Azərbaycan
Azərbaycan Рэспубліка Беларусь
Рэспубліка Беларусь Република България
Република България  Bosna i Hercegovina
Bosna i Hercegovina  Česká republika
Česká republika საქართველოს
საქართველოს Republika Hrvatska
Republika Hrvatska  Kosovo
Kosovo  Қазақстан
Қазақстан  Кыргыз Республикасы
Кыргыз Республикасы  Latvija
Latvija Lietuva
Lietuva Magyarország
Magyarország  Moldova
Moldova  Република Македонија
Република Македонија  România
România  Rzeczpospolita Polska
Rzeczpospolita Polska Република Србија
Република Србија  Российская Федерация
Российская Федерация  Republika Slovenija
Republika Slovenija  Slovensko
Slovensko Тоҷикистон
Тоҷикистон Türkmenistan
Türkmenistan Україна
Україна
